FACT Benefits
Insight into an organization's least understood risks

Safeguarding Trust
To perform safely and efficiently, companies operating in critical industries depend on instrumented, interconnected, and intelligent embedded devices.
Since a “smart” device is only as good as the firmware or software running on it, asset owners must rely on their vendors to supply valid, authentic software for system implementation and upgrades.
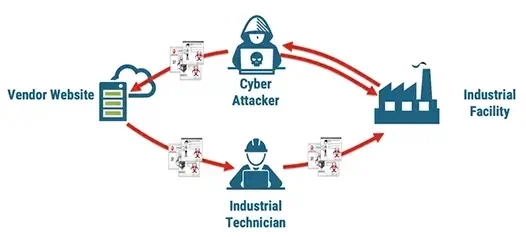
Of course every vendor does its best to supply safe and reliable software. But the path from device vendor to device user - the software supply chain - can be complex and open to exploitation.
Unfortunately, events like the Dragonfly attacks and more recently the Kaseya attacks make it clear that criminal groups and hostile governments are exploiting the weaknesses in our software distribution processes. They have begun to develop and distribute counterfeit software for embedded systems.
If a technician installs just one malicious file, this Trojanized software can have access to everything in your system. The consequences of this kind of attack can be devastating.
Let's get in touch so we can show you how to gain software supply chain visibility at scale.
Addressing Complexity Challenges
Industry currently lacks a robust solution for protecting organizations — both suppliers and asset owners — from supply chain attacks.
When you examine the upgrade process in large organizations, it’s easy to see the current challenges:
- Most asset owners use devices sourced from a wide variety of vendors.
- Every vendor includes software subcomponents sourced from 3rd parties.
- Every vendor has its own software distribution and validation process.
- Every system has its own upgrade process.
- Technical staff obtain software updates from multiple sources, including websites, USB drives, contractors, and distributors.
- Intelligent devices need regular updates to stay secure, yet are widely distributed throughout factories and equipment.
The concern over counterfeit software and firmware isn’t hypothetical. And the resulting problems from an attack are both life threatening and expensive.
See how FACT Trust Scores provide visibility into your entire software supply chain
