FACT for Asset Owners
Continuous assurance of your software supply chain
The Software Supply Chain Problem
If you work in a high tech market — such as Energy, Oil & Gas, Manufacturing, Medical, or Aerospace — your company probably has hundreds of “smart" systems that provide vital control or data collection functions every minute of every day.
Each of these systems contains hundreds of "smart" devices. And each of these devices contains multiple software, firmware, and configuration files.
So you probably have thousands of different files — sourced from hundreds of different vendors, consultants, and staff — that all must be valid and secure to run your factory (or patient care system or aircraft) safely. These complex dependencies are your software supply chain.
If cybercriminals or hostile governments can trick your staff into installing a modified version of just one of these files, then your company secrets, your operations, and your team are all at risk.
Managing firmware and software in “smart” devices is complicated. Most companies use products from a variety of different suppliers, each offering a different way of delivering and installing updates. Upgrade workflows involve numerous staff roles dependent on location and function. And traditional IT controls, such as code signing, are rarely an option — especially on legacy devices.
Do you know the security profile of your software suppliers? Do they provide SBOMs?
Secure Your Software Supply Chain from Cyberattacks
FACT simplifies software upgrade processes and makes them more secure and reliable.
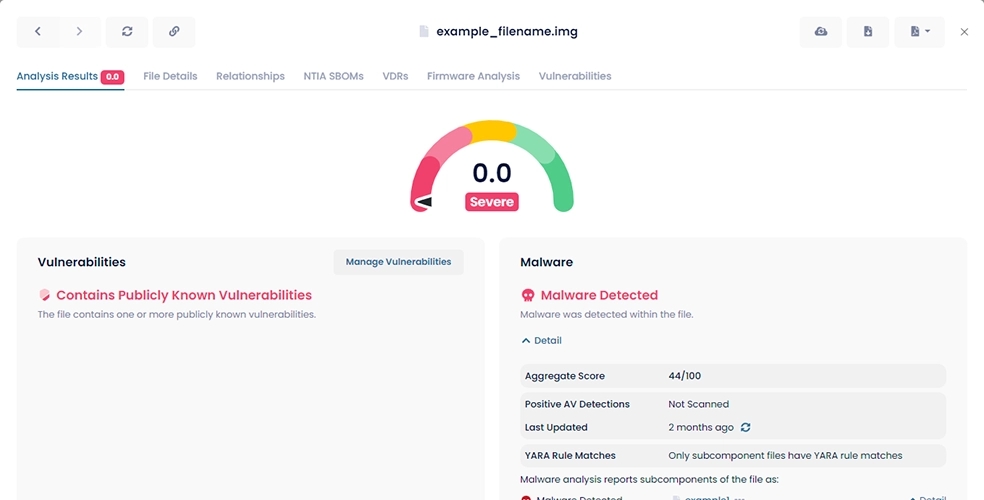
When your team receives a file from any source — the web, a USB drive, a contractor — they can use FACT to ensure the file is identical to the original. We also assign the file an easy-to-use Trust Score. The Trust Score will let you know if we've detected any security issues like vulnerabilities, malware, or improperly signed certificates, and you can drill down to find more details.
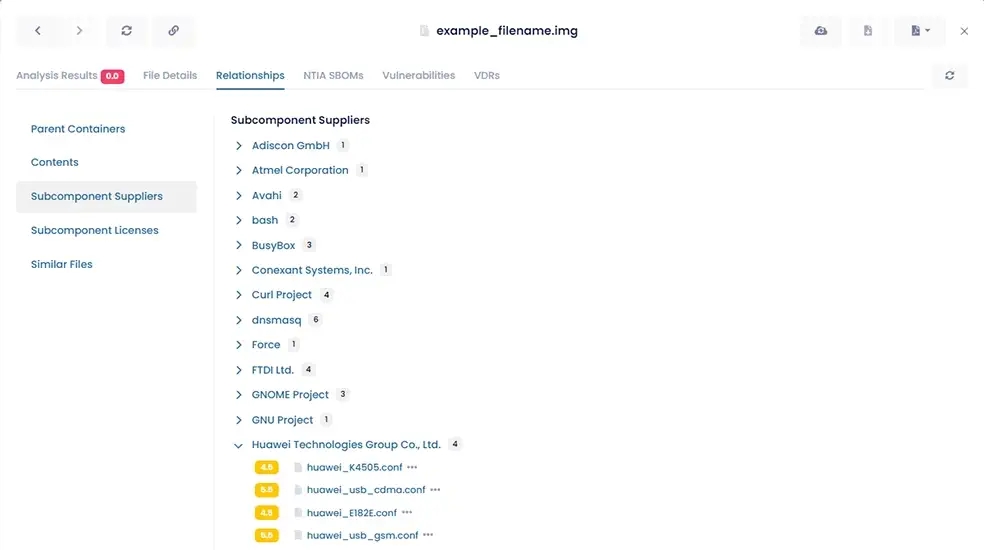
aDolus works directly with equipment vendors to collect "fingerprints" of original files before they are released to the market. We also dig deep into each file's structure to determine if any subcomponents contain known vulnerabilities or malware issues.
Finally, FACT's role management and reporting features give you full visibility into the software and firmware being deployed on your most critical systems. Trust scores help you make and enforce policies regarding which files should not be installed on critical systems.
You decide exactly what software, firmware, or configurations meet your company's requirements.
Are your upgrade and patching processes secure and reliable?
Let's get in touch so we can show you what FACT can do for asset owners.
FACT Platform Features
Benefits
Continuous Supply Chain Visibility
- Advanced aggregation, analytics, and correlation
- Software validation and easy-to-use scoring
- Malware detection via multiple AV engines and over 18,000 YARA rules
- Certificate chain and signature validation
- Up-to-date cybersecurity risk intelligence
- Gain detailed visibility into all the vendors, products, and components across all your assets
- Gain confidence in your supply chain with independent validation
- Reduce the risk of ransomware
- Reduce the time spent on false-positives
SBOMs
- 1-click NTIA-compliant SBOMs in approved formats
- Enriched SBOMs offering drill-down-and-around to expose vulnerable components across all your assets
- AI-driven searching of SBOMs to discover hidden high-risk components
- Focus efforts on exploitable vulnerabilities
- Provide audit evidence for regulators
- Gauge the quality of your vendors' security practices
- Assess how frequently components are updated
- Reduce costs through intelligent risk-based patching
Vulnerability Management
- Continuous monitoring of public and supplier alerts
- Natural language processing to extract data buried in text-based alerts
- Probabilistic detection of hidden vulnerabilities
- Assess the risk from high-profile vulnerability announcements
- Find vulnerabilities in all software in minutes, not days
- Reduce costs through automated vulnerability research
Risk and Compliance Management
- Executive reporting and KPIs
- 3rd-party supplier discovery
- Supplier quality assessments
- Risk profiles by product line/supplier
- Detection of high-risk software and components
- Make cyber-informed procurement decisions
- Avoid high-risk or blacklisted suppliers or countries
- Enforce policies regarding updates on critical systems
- Protect your brand and reduce potential liability
- Provide in-depth analysis for M&A teams
Scalability, Security, Performance
- Full-featured RESTful API
- Cloud (SaaS) platform with portal
- Vendor-, platform-, and operating system-agnostic
- 11 billion analysis operations/day
- 1.4 billion mapped relationships between parent-child files
- Address IT, IoT, and OT products with a single solution
- Integrate with corporate systems, workflows, and processes
- Enable secure digital transformation
- Be assured thanks to proven AWS security best practices
aDolus FACT Supply Chain Assurance
FACT Keeps Your
System Safe
Are your upgrade and patching processes secure and reliable?
Manage Development & Deployment Risk
FACT gives you visibility and control over firmware and software deployments on critical systems with enriched SBOMs.
Manage Support Ops & Distribution Chain Risk
FACT provides independent validations that the software you’ve got is authentic, tamper-free, and safe to install on critical systems.