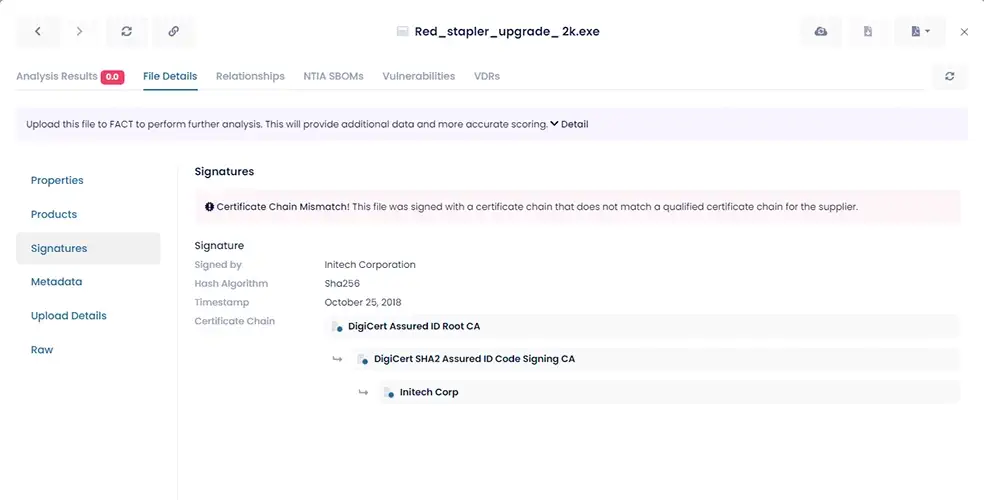
Certificate Validation
Assurance that software is authentically signed
Detect Certificate Chain Mismatches and Fraudulently Signed Packages
Code signing is a very useful technology for determining if software is authentic. However, without the proper checks, attackers can misuse signing to create a false sense of security in their victims.
The mere existence of a digital signature is not proof that the software is trustworthy because:
Software can be digitally signed with keys stolen from legitimate companies
Malware can be signed using certificates mistakenly issued to malicious actors impersonating legitimate companies
Code signing and digital certificates are necessary but not sufficient to ensure software is tamper-free and legitimate.
Researchers showed that there are currently over one million malware files in the wild that are signed. Unfortunately, they are signed by bad actors as a means of fooling antivirus software.
FACT tests packages for signs of illegitimate code signing.
Let's get in touch so we can show you how FACT validates certificate chains.
Validate Unsignable Packages
While most Windows and Linux files can be signed, many files, such as binaries and DLLs, cannot. ICS environments need a way to trust software and firmware that cannot be signed and FACT allows you to authenticate these unsignable files.
Detect Stolen Keys
FACT helps vendors discover if a bad actor is distributing software using their credentials. Once a vendor becomes aware this is happening, they address the situation (such as by contacting the certificate authority and alerting their customers). Minimizing the impact of stolen credentials is an important part of reputation protection.