SBOM Creation
Enriched Software Bill of Materials
What Is an SBOM?
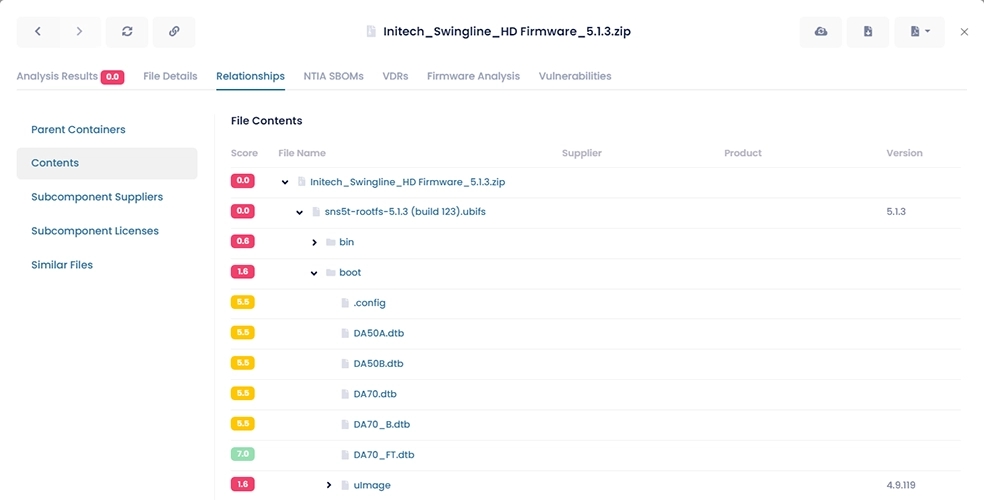
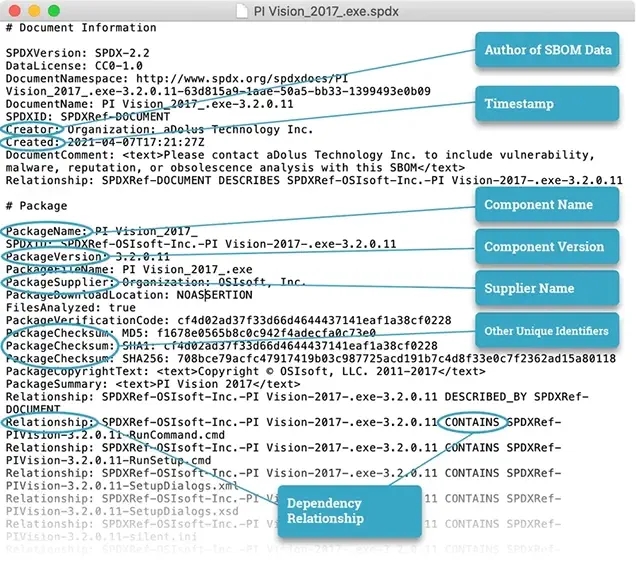
A Software Bill of Materials (SBOM) is a nested list of the ingredients in a software package, and it is becoming the key tool in the fight to reduce risks to the software supply chain.
The NTIA (National Telecommunications and Information Administration) has defined an SBOM as:
"... a formal record containing the details and supply chain relationships of various components used in building software ...
... An SBOM provides those who produce, purchase, and operate software with information that enhances their understanding of the supply chain, which enables multiple benefits, most notably the potential to track known and newly emerged vulnerabilities and risks."
Generate SBOMs with a Single Click
Attempting to manually compile an SBOM would be costly, time-consuming, and prone to errors.
With the SBOM creation feature in our FACT Platform, you can:
Generate fully NTIA-compliant SBOMs with one click of a button
Vastly reduce the time and effort to create accurate SBOMs
Derive SBOMs from binaries and legacy software where source code is no longer available
Support for Recognized Standards
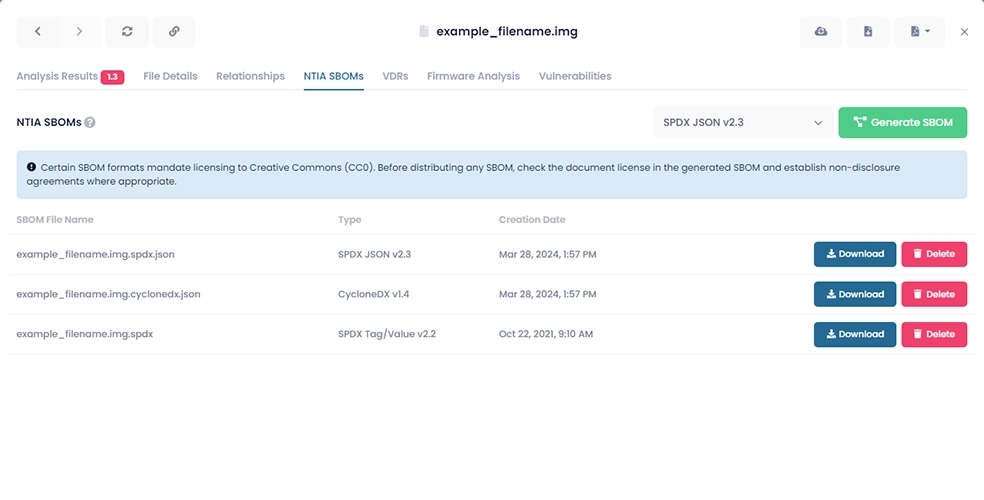
Recent work done by the NTIA on defining the minimum components of an SBOM has identified three supported formats:
- SPDX (Software Package Data eXchange)
Both SPDX JSON v2.3 and SPDX Tag/Value v2.2 are fully supported by FACT.
- CycloneDX
CycloneDX v1.4 is fully supported by FACT.
- SWID
Please contact us for more information.
Note that the advancement of SBOMs, including scaling and operationalization, has transitioned from NTIA to CISA (Cybersecurity and Infrastructure Security Agency).
Ask us about how to produce compliant SBOMs.
Satisfy Regulatory Requirements
The regulatory landscape is rapidly expanding in the wake of high-profile supply chain cyber attacks like SolarWinds and Kaseya.
Executive Order 14028 in the U.S. directs all government agencies to require SBOMs from their suppliers of critical software. Evidence suggests the private sector won’t be far behind.
Regulators in specific industries have their own regulations governing supply chain security (such as NERC CIP-013 in the power utility industry or FDA-2018-D-3443 in the medical industry). Using FACT provides evidence of a proactive cybersecurity program.
Meet the Increasing Demand for SBOMs
Now that SBOMs have been defined and mandated for U.S. government agencies, purchasers of critical software are also expecting vendors to disclose the contents of their products through SBOMs.
Without an SBOM, asset owners assume all the risk associated with software. Just as occurred in the banking industry, purchasers should expect some kind of compensation for the assumption of that risk.
Government agencies now require SBOMs, and asset owners will expect the same now that they know they're available.
Vendors who can supply SBOMS to customers gain a competitive advantage.
FACT enables vendors to quickly and securely satisfy customer requests for secure SBOMs.